China Internet censorship in 2023 - common methods to censor the internet part 1

Author
GoClickChinaIn other articles, we have discussed how Internet censorship affects businesses both locally and globally, but we have not delved into the methods governments use to exercise such censorship. That is why we have prepared this blog post where we will explore the main internet content blocking techniques.
Methods to block and filter content on the Internet
Thanks to the power and efficiency of today’s microprocessors and advances in the fields of Natural Language Processing (NLP), Artificial Intelligence (AI), Machine Learning (ML), and Edge Computing, the methods used to censor online content are more effective than ever. Below, we will take a closer look at each of them.
IP and Protocol-based blocking
-
Affected users/services. This method is highly efficient when the service or content is hosted on a server with a static IP address. It is also effective for blocking known IP ranges (for example, a particular country or province).
-
Level of unintentional blocking produced. High. All websites hosted on the affected server will be blocked. Considering that most websites use shared hosting, the collateral damage of this method can be devastating.
-
Effectiveness in blocking content. Low. Since this method is based on IP addresses and TCP/IP ports, it is complex to maintain up-to-date rules of addresses and ports to block. That said, this method is very effective in blocking traffic from the IP addresses included in those rules.
-
Can it be circumvented?. Yes. Users can use a Virtual Private Network (VPN) to mask the IP address and protocol. Content creators can manually change the IP address of their server to circumvent this control and use content delivery networks (CDNs) for that purpose. However, keep in mind that this is like playing cat and mouse. Regulators block IP addresses daily, and those affected must act accordingly.
This method works similarly to a conventional firewall. The purpose is to monitor incoming/outgoing network traffic to apply rules that may include blocking specific IP address ranges or TCP/IP ports. Today, both home and enterprise-grade routers come with this kind of firewall functionality. Moreover, most Linux servers use packages such as iptables to achieve this exact purpose.
Implementing this technique is relatively simple. The regulator only needs to place the firewall device between the end-user and the content to block; that’s why the preferred location is at ISP-level. Since all network traffic passes through the firewall, blocking certain protocols, ports, or IP addresses is easy.
A variant of this method is known as bandwidth throttling, which limits the flow of traffic to certain IP or TCP/IP ports instead of blocking it. This method is widely used by Internet Service Providers (ISPs) around the world when they detect torrent downloads and other content/protocols they consider “inappropriate.” From a censorship perspective, bandwidth throttling effectively discourages access to certain content because the connection speed to such sites is so low that it renders them inoperable.
Deep Packet Inspection-based blocking
-
Affected users/services. This strategy is very effective when the regulator has absolute control over Internet access and wishes to block/restrict certain types of traffic such as torrents, VoIP, or easily identifiable content using keywords.
-
Level of unintentional blocking produced. Medium/low. Although this method is more selective than the IP-blocking technique, it can cause a lot of collateral damage depending on its configuration. For example, if VoIP traffic is blocked, an entire nation could be left without this service.
-
Effectiveness in blocking content. The efficiency of this method depends on many variables. The better identified the content/traffic pattern to be blocked, the higher the efficiency. Some patterns are simple to recognize, while others are more complex. In terms of content, keywords are often used to alert the system about “inappropriate” content. In this sense, the most advanced deep packet inspection systems are supported by AI and ML to make detection more efficient.
-
Can it be circumvented?. Yes. As well as the IP-based method, using VPNs that encrypt the traffic makes it very difficult to apply this technique. However, this only solves the problem for users who want to surf the Internet. For websites and applications, circumventing this control is much more difficult.
The technique known as deep packet inspection (DPI) is far more sophisticated than the one discussed in the previous point. This is because it literally analyzes network traffic for known patterns or specific keywords. As expected, this type of inspection consumes a lot of resources to the point that it can become a bottleneck in the network.
Aside from the inconvenience of the resources required, DPI has been used for years by companies around the world to protect against spam, malware, viruses, and data leaks. In this type of scenario where all company traffic passes through DPI-capable devices, the effectiveness of blocking unwanted traffic and content has been high. For this reason, regulatory agencies in different countries have adopted this strategy.
However, it should be emphasized that the effectiveness of deep packet inspection is variable and depends largely on the accuracy of the patterns or keywords used. Like IP-based blocking, this method requires absolute control of the Internet access infrastructure to ensure that all content passes through this filtering.
URL-based blocking
-
Affected users/services. This type of blocking affects specific blacklisted websites and web applications. Because of this, it is not very effective in blocking services such as VoIP or torrents.
-
Level of unintentional blocking produced. Low. Generally, the collateral damage produced by this method is very low since it is limited to blocking the blacklisted URLs. However, it may happen that a misconfiguration of the keywords causes an unwanted blocking on other websites.
-
Effectiveness in blocking content. The effectiveness of URL-based blocking depends basically on two factors. On the one hand, the ability to intercept all traffic between the parties involved and on the other hand the correct configuration of the blacklist. Since URLs do not change as often as IPs, this mechanism is efficient in blocking content from high-level URLs. For example, if “Google” is used as a keyword, google.com, google.it and google.es will be blocked. However, when it comes to deep links, such as blog posts, URL blocking can fail.
-
Can it be circumvented?. Yes. It can be evaded. A simple way to bypass this kind of blocking is to use a VPN that encrypts the traffic. When the traffic is encrypted, the proxy responsible for filtering the content cannot see the URL but only the IP, so it is not effective.
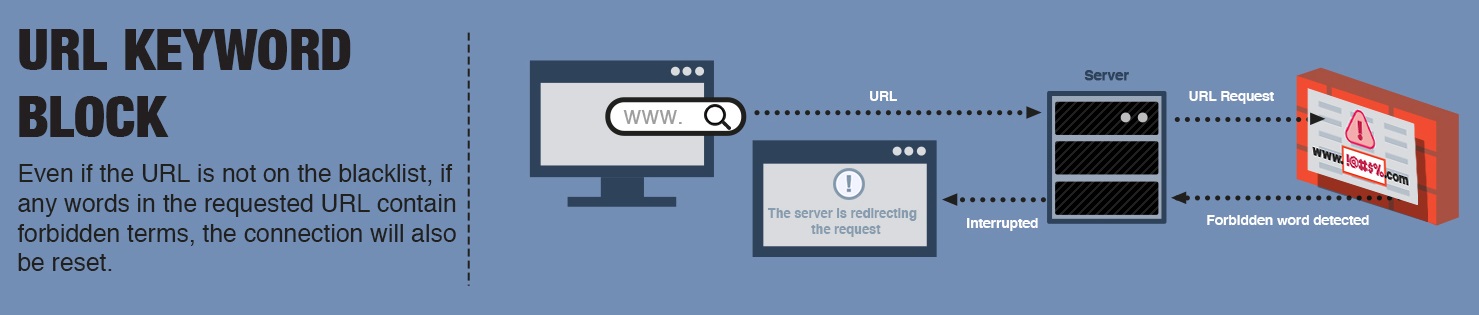
While URL-based blocking can be effective in blocking the content of web pages and services deemed inappropriate, in practice, they are so costly to maintain that they are not so popular with regulators. That said, when used properly, they can be combined with deep packet blocking and IP-based blocking to complement their weaknesses and achieve greater efficiency.
Platform-based blocking
-
Affected users/services. This method only affects platforms or services that agree to collaborate with regulators to filter content.
-
Level of unintentional blocking produced. Very low. Since the platforms themselves filter the content, the level of collateral damage is minimal.
-
Effectiveness in blocking content. Although there is no official data to verify the effectiveness of this method, it’s known that the platforms that are subjected to this type of censorship usually comply with the demands of the censor to remove certain types of content (in the case of Facebook or Twitter) or block certain search results (in the case of search engines such as Google or Bing). That said, this technique is easy to evade, so its real-world effectiveness is almost nil.
-
Can it be circumvented?. Yes, it can be circumvented. Since filters on search results or content are implemented by a specific platform, a simple way to circumvent this censorship is to switch search engines. Another simple method to circumvent these content controls is to use a VPN that connects the user from another country where such filters do not exist.
Platforms such as Google, Facebook, Bing, Twitter, and Instagram have long used filters to block content related to pornography, violence, racism, and other sensitive topics. Governments around the world often require additional restrictions to be added to these filters according to their legislation. So you can think of this type of censorship as a complement to what the platform already uses by default. Having said that, experience shows that the effectiveness of this kind of blocking is very low. Look at it this way; search engines cannot block banned content as such; they can only remove it from the search results. So it is enough to use an alternate search engine (or a VPN connection to another jurisdiction) to circumvent the blocking.
Part 2
In the second part of this article, we will look at other commonly used methods for blocking or filtering the internet, namely DNS-based blocking, network shutdown, VPN blocking, manual and A.I. censorship. We will also discuss the content blocking mechanism.


